Physical extraction is the highest level of extraction and is also the most complicated. It copies the entire contents of the memory in a bit by bit fashion. This means that in most cases, it can retrieve not only the active / live data but also deleted text messages, photos and other files not indexed in the phone file system.
Physical extraction is not an easy process as it depend on the operating system of the mobile phone as well as the security measures incorporated by the manufacturer to prevent reverse engineering.
But the best thing about physical extraction is that it leaves no trace that the data has been extracted.
Sometimes, the phone is so damaged that it cannot display data, or be powered on. In these cases, we need to perform physical extraction using a variety of methods. We may use EDL mode or actually chip off the memory using specialised hardware. With older phones, the JTAG interface may also be used to extract data.

Logical extraction is the quickest way to extract data from mobile phones. The forensic investigator connects to the mobile phone through USB, Bluetooth etc and attempts to extract data.
Most live data can be extracted through logical extraction. The software connects through APIs and gets the different kinds of files on memory including:
This process has write protection to maintain data integrity and ensure that evidence is legally admissible in court. Specific partitions can be chosen for extraction as well as directories / files / categories of data. All feature phones and smartphones are supported.
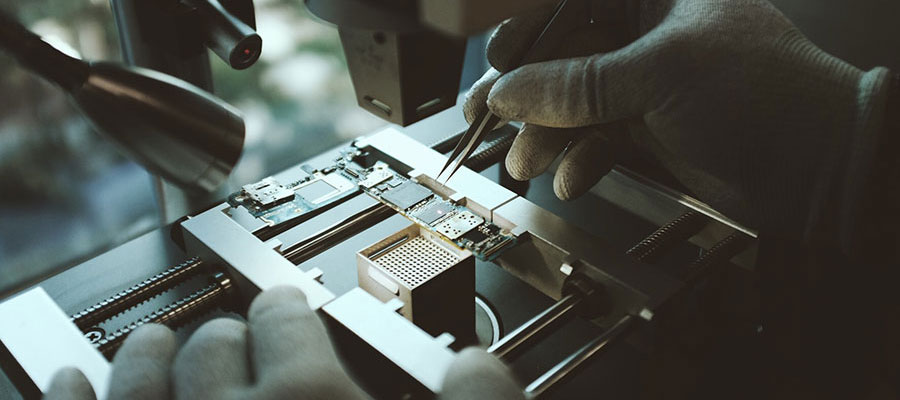
This is the data extractiion method of last resort. When all other attempts fail, including logical / physical / JTAG, we usually do a chip off extraction. This means that the phone memory is actually “chipped off” from the IC and read with an external memory reader.
Even if a phone has undergone catastrophic damage, we can still do a chip off and the success rate is usually above 90%. However, this is a very intrusive method and it implies that once the memory is chipped off, the phone cannot be repaired.
We use specialised forensic hardware to perform the chip off. As it’s a delicate and complicated operation, our team takes around two weeks to complete the extraction and report generation process. There is also a certain level of risk involved due to the physical nature of the extraction and our team will advise you on whether it’s appropriate to move ahead with the removal or not.
Once the memory is removed, data will extracted from it and analysed using our regular forensic software.

This is an advanced method of extracting data from mobile phones using TAPs (Test Access Ports). The complete physical image of the data can be extracted using JTAG.
JTAGging is a very intensive process. So it’s used when logical / physical extraction is no longer possible. When a mobile device has suffered external damage but the motherboard still works, an examiner can connect to the motherboard through JTAG and get the data. This method is also useful for pattern locked phones or those phones with the data port internally disabled by the carriers / users.
JTAG requires a thorough understanding of the TAPs on the phone, which differ from manufacturer to manufacturer. The phone’s PCB may need to be examined when the TAPs are unknown or the documentation is insufficient or unavailable. Wire leads need to be soldered on to connect to the JTAG emulator.
The memory can then be read by instructing the processor through the JTAG emulator. Once the physical image is extracted, it can then be analysed by the forensic report software.
As JTAG is a complicated, long drawn process, our team will take a minimum of 7-10 days to complete the extraction. If you want a JTAG extraction, please allow at least two weeks time for getting a forensic report.
Copyright © 1996 - 2023 ZOOM CyberSense. All Rights Reserved.